 Modern Endpoint Detection & Response (EDR) products rely heavily on user‑mode API hooking to monitor process behavior. However, there is a critical window during process initialization where these hooks are not yet active. Adversaries exploit this by using “early” injection techniques to execute code before the security instrumentation can initialize.
Modern Endpoint Detection & Response (EDR) products rely heavily on user‑mode API hooking to monitor process behavior. However, there is a critical window during process initialization where these hooks are not yet active. Adversaries exploit this by using “early” injection techniques to execute code before the security instrumentation can initialize.
This article examines two significant methods for achieving this: the classic Early Bird Injection and the more advanced Early Cascade Injection.
Early Bird Injection
Early Bird Injection is a stealthy variation of Asynchronous Procedure Call (APC) injection. It targets a process in its infancy to ensure the malicious payload runs before the EDR’s user-mode hooks are in place.
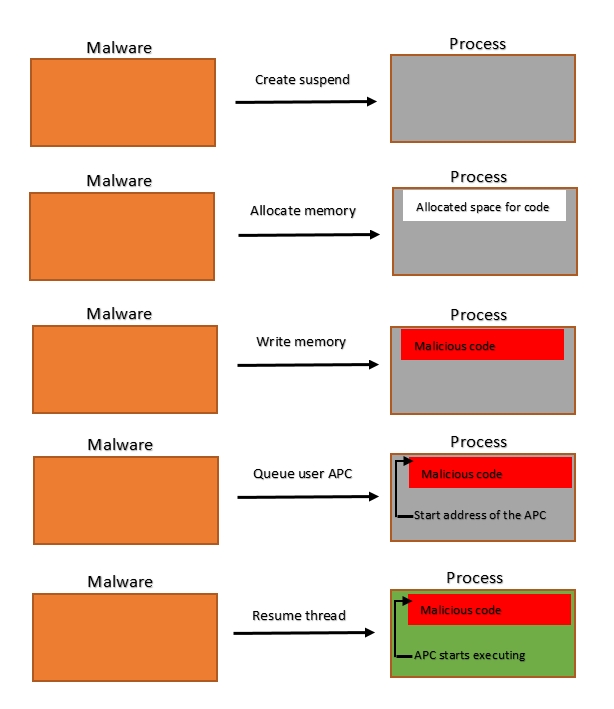
Core Idea
The technique exploits the state of a process created with the CREATE_SUSPENDED flag. Because the main thread has not yet started, it provides a perfect environment to stage an APC.
- Create Suspended Process: A legitimate process, such as
svchost.exe, is started in a suspended state. - Allocate & Write: Memory is allocated in the target process, and the shellcode is written to that space.
- Queue APC: The
QueueUserAPCfunction points the main thread to the shellcode. API is also discussed here - Resume Thread: When the thread resumes, the system triggers the APC immediately, executing the malicious code before the thread reaches its original entry point.
This technique has been used by several malware families, including TurnedUp (APT33), Carberp, and DorkBot.
Early Cascade Injection
Developed by Outflank, Early Cascade Injection is a novel evolution designed to be even stealthier than Early Bird. While Early Bird relies on suspicious APC queuing, Early Cascade integrates into the natural DLL loading flow of a process.
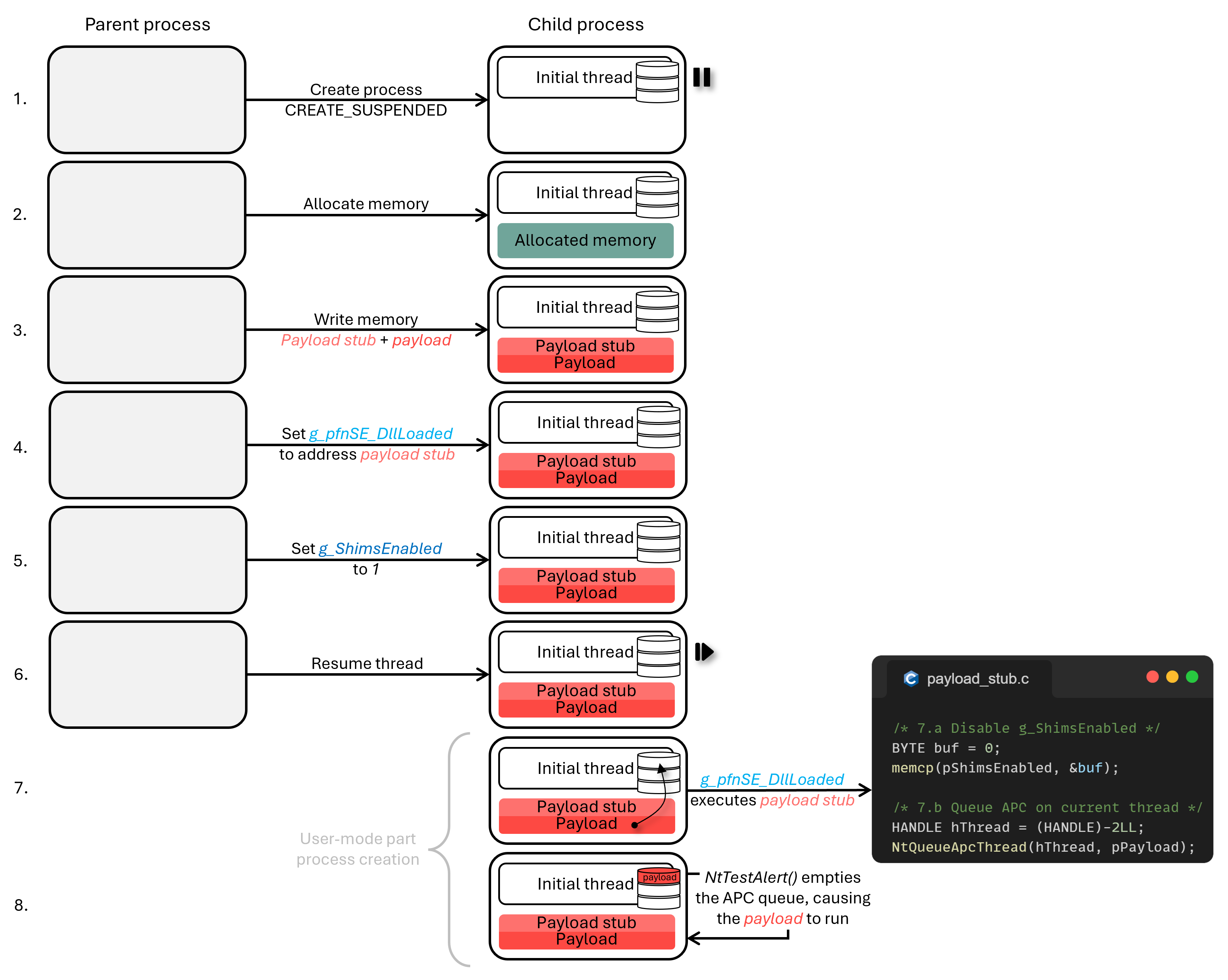
Core Idea
Early Cascade targets the LdrInitializeThunk function in ntdll.dll. This function is responsible for initializing the process environment and loading essential DLLs.
- Intercept LdrInitializeThunk: The technique hooks or manipulates the
LdrLoadDllfunction during the initialization phase. - DLL Load Cascade: The malicious code or DLL is injected as part of the normal module loading process.
- Bypass EDR Initialization: Most EDRs initialize their hooks after
kernel32.dllandkernelbase.dllare loaded. Early Cascade strikes before this point.
By avoiding cross-process APCs and minimizing remote interaction, this technique blends in with legitimate process startup behavior.
Quick Comparison
| Feature | Early Bird Injection | Early Cascade Injection |
|---|---|---|
| Primary Mechanism | Queues an APC to a suspended thread | Intercepts LdrInitializeThunk |
| Remote Interaction | Uses QueueUserAPC (higher risk) |
Minimizes remote interaction |
| Stealth Strategy | Executes before main thread | Blends with DLL loading cascade |
| Common Use | APTs and banking trojans | Red Team tools (Outflank C2, ShovelNG) |
Defensive Relevance
Detecting these techniques requires visibility beyond standard user-mode hooks. Defenders should implement:
- Kernel-mode Monitoring: Monitor DLL load sequences and early-stage thread activity from the kernel.
- Behavioral Analysis: Baselining process startup to detect unusual patterns, such as
CREATE_SUSPENDEDfollowed by memory allocation and APC queuing. - Memory Scanning: Scanning for anomalous modules or shellcode that may have been loaded during the initialization phase.
References
- Outflank: Introducing Early Cascade Injection
- Outflank: EarlyCascade Extension and More
- Cyberbit: New ‘Early Bird’ Code Injection Technique Discovered
- xbzon.sh: Mythic C2 with EarlyBird Injection
- Red Team Notes: Early Bird APC Queue Injection