In this article we will dive into Cyber Kill Chain and MITRE ATT&CK. After getting comfortable with both frameworks, a short combination of both will be shown. The fishbone model is still under construction.

The offense sells tickets. Defense wins championships
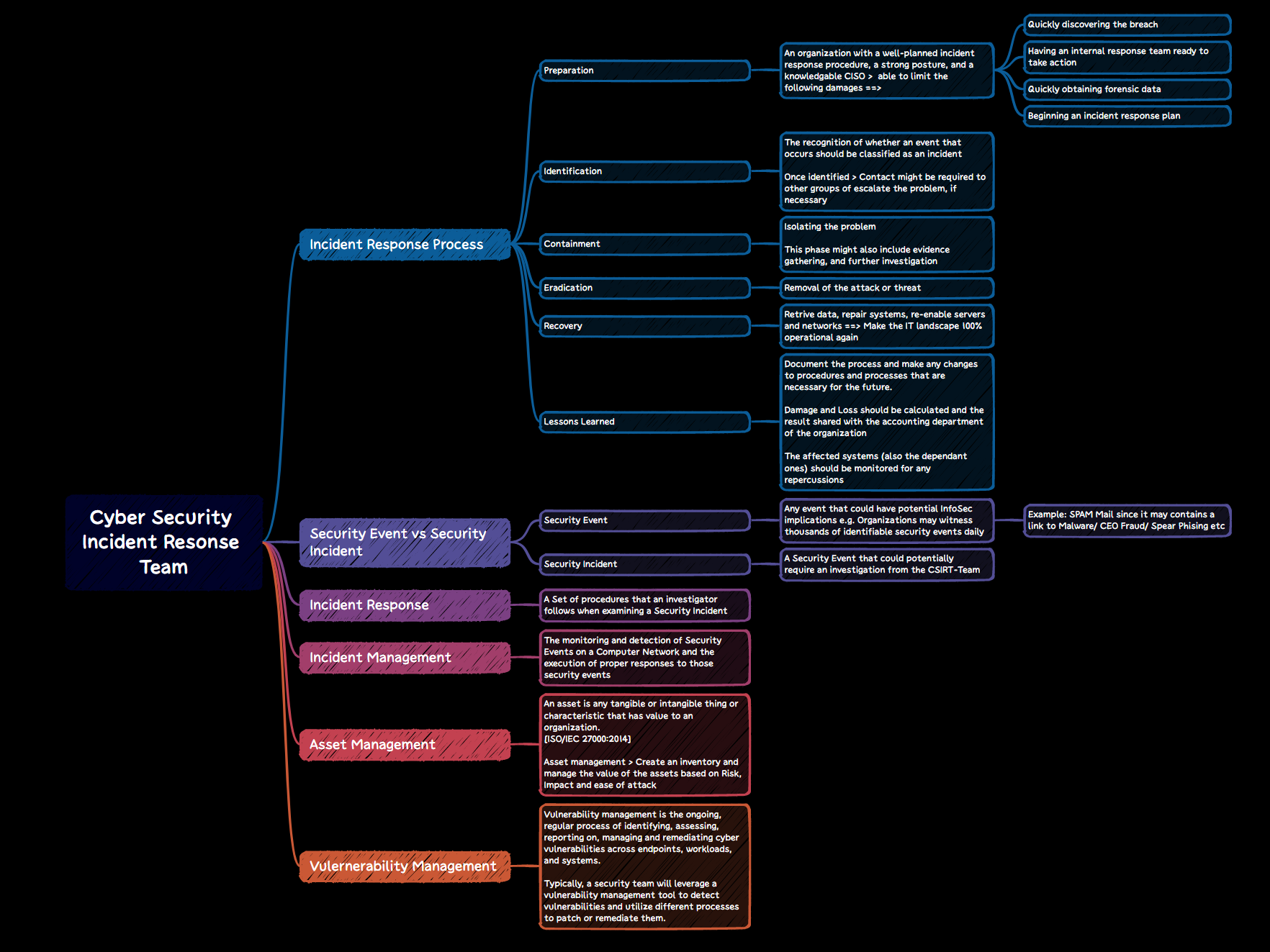
CSIRT
Dockerized/AWS Splunk Attack Range Lab
 If you strife like me constantly to become better and looking for chances to train this one is for you. With Attack Range you can easily replay common attacks based on the MITRE ATT&CK Framework. Make sure that you check out splunk/attack_data to understand the magic of this solution.
If you strife like me constantly to become better and looking for chances to train this one is for you. With Attack Range you can easily replay common attacks based on the MITRE ATT&CK Framework. Make sure that you check out splunk/attack_data to understand the magic of this solution.
ProxyNotShell - Scan and Mitigate
In this post you’ll find a way how to systematically find and kill possible open flanks regarding CVE-2022-41082 and CVE-2022-41040.
Linux Hardening - etckeeper
 A versioning of configuration directories is meaningful from documentation and backup view. Thus all changes to configuration files are logged and versioned, in addition earlier versions can be restored in the case of error. Completely without caution these features are not to be enjoyed, since protectable information is in the etc directory. Encryption and restrictive file permissions when transferring or backing up the repo in which the etc directory is versioned should therefore be taken into account. This article shows the versioning with the software etckeeper with git.
Table of Contents
A versioning of configuration directories is meaningful from documentation and backup view. Thus all changes to configuration files are logged and versioned, in addition earlier versions can be restored in the case of error. Completely without caution these features are not to be enjoyed, since protectable information is in the etc directory. Encryption and restrictive file permissions when transferring or backing up the repo in which the etc directory is versioned should therefore be taken into account. This article shows the versioning with the software etckeeper with git.
Table of Contents
Internet-Facing Attack Surface
 Based on the internet-facing applications of your corporate, you can derive the attack surface and look through the eyes of an attacker. With this post I’ll try to do some definitions, explain why, and give some best practices how you could adopt it to the cloud.
Based on the internet-facing applications of your corporate, you can derive the attack surface and look through the eyes of an attacker. With this post I’ll try to do some definitions, explain why, and give some best practices how you could adopt it to the cloud.
Active Directory - Hardening and hunting
CCDC Notes
Log Review Cheatsheet Critical Log Review Checklist for Security Incidents
Windows Security Events
 Windows Security Event Codes, also known as Event IDs, are numeric codes that are used to identify specific events in the Windows event logs that are related to security. These codes are generated by the Windows operating system and can be used to track and troubleshoot security-related issues.
Windows Security Event Codes, also known as Event IDs, are numeric codes that are used to identify specific events in the Windows event logs that are related to security. These codes are generated by the Windows operating system and can be used to track and troubleshoot security-related issues.
CyberChef Introduction
Below you’ll find a quick introduction into CyberChef, it’s UI, and a example. CyberChef can be used to: Encode, Decode, Format data, Parse data, Encrypt, Decrypt, Compress data, Extract data, perform arithmetic functions against data, defang data, and many other functions.
CyberChef Recipes CheatSheet
 CyberChef is the ‘Cyber Swiss-Army Knife’ for Security Analysts created by GCHQ. The tool pretty much helps for tasks like data transformation, extraction, and manipulation all in your web-browser.
CyberChef is the ‘Cyber Swiss-Army Knife’ for Security Analysts created by GCHQ. The tool pretty much helps for tasks like data transformation, extraction, and manipulation all in your web-browser.
AWS CloudTrail events for Incident Response
Writeup of critical CloudTrail events, that can be used for Incident Response purposes or Detection Engineering
AuditD Config
 🔒 Unlocking the Secrets of Digital Fortresses for your Unix. This is just my way to get into the topic of AuditD by writing my own one.
🔒 Unlocking the Secrets of Digital Fortresses for your Unix. This is just my way to get into the topic of AuditD by writing my own one.
PowerShell RTR Snippets
 Empower Your Defense with PowerShell: Real-Time Response (RTR) Snippets for Windows and Azure AD. Enhance the incident response capabilities with these practical PowerShell snippets for Windows and Azure AD. Leverage these time-tested tools to effectively defend your IT infrastructure which helped me already in the past.
Empower Your Defense with PowerShell: Real-Time Response (RTR) Snippets for Windows and Azure AD. Enhance the incident response capabilities with these practical PowerShell snippets for Windows and Azure AD. Leverage these time-tested tools to effectively defend your IT infrastructure which helped me already in the past.
Zero Trust Journey
 This blog post provides an overview of Zero Trust principles and their implementation in a security-conscious organization. It’s crucial to continually align your security practices with evolving threats and challenges in today’s digital landscape.
This blog post provides an overview of Zero Trust principles and their implementation in a security-conscious organization. It’s crucial to continually align your security practices with evolving threats and challenges in today’s digital landscape.
SBOM - Software Bill Of Material
 Journey and quick overview related to SBOM (Software Bill of Materials) to highlight why it matters related to supply chain attacks.
Journey and quick overview related to SBOM (Software Bill of Materials) to highlight why it matters related to supply chain attacks.
DFIR - Digital Forensic Incident Response
 Digital Forensics and Incident Response (DFIR) is a field within cybersecurity that focuses on the identification, investigation, and remediation of cyber attacks.
Digital Forensics and Incident Response (DFIR) is a field within cybersecurity that focuses on the identification, investigation, and remediation of cyber attacks.
Cuckoo Sandbox
 Guide for setting up a Cuckoo Sandbox for malware analysis on Ubuntu & Windows VMs. It covers VM setup, network configurations, software installations, and troubleshooting tips. The content includes detailed steps, links to references, and helpful resources for an effective setup.
Guide for setting up a Cuckoo Sandbox for malware analysis on Ubuntu & Windows VMs. It covers VM setup, network configurations, software installations, and troubleshooting tips. The content includes detailed steps, links to references, and helpful resources for an effective setup.
NMAP for Incident Response
 This post covers the versatile uses of NMAP, exploring target enumeration, host discovery, port scanning techniques, version and OS detection, traceroute, script scanning, varied output formats, and NMAP port states. It’s a comprehensive guide to leveraging NMAP effectively in incident response scenarios, citing insights from “NMAP Network Scanning by Gordon ‘Fyodor’ Lyon
This post covers the versatile uses of NMAP, exploring target enumeration, host discovery, port scanning techniques, version and OS detection, traceroute, script scanning, varied output formats, and NMAP port states. It’s a comprehensive guide to leveraging NMAP effectively in incident response scenarios, citing insights from “NMAP Network Scanning by Gordon ‘Fyodor’ Lyon
Shodan for Defenders
 Shodan, a search engine for finding internet-connected devices. This post covers basic search commands, the Shodan Command Line tool, and incident response tactics for detecting Cobalt Strike Servers, Metasploit, Empire, and Responder. It includes valuable resources and cheat sheets for further exploration.
Shodan, a search engine for finding internet-connected devices. This post covers basic search commands, the Shodan Command Line tool, and incident response tactics for detecting Cobalt Strike Servers, Metasploit, Empire, and Responder. It includes valuable resources and cheat sheets for further exploration.
Windows ETW (Event Tracing for Windows)
 Event Tracing for Windows (ETW) provides a mechanism to trace and log events that are raised by user-mode applications and kernel-mode drivers. ETW is implemented in the Windows operating system and provides developers a fast, reliable, and versatile set of event tracing features. These logs are also forming a crucial baseline for EDR/XDR solutions to detect suspicious or malicious behavior by integration with the operating system.
Event Tracing for Windows (ETW) provides a mechanism to trace and log events that are raised by user-mode applications and kernel-mode drivers. ETW is implemented in the Windows operating system and provides developers a fast, reliable, and versatile set of event tracing features. These logs are also forming a crucial baseline for EDR/XDR solutions to detect suspicious or malicious behavior by integration with the operating system.
iptables - Firewall Management Script
 This Bash script is designed to facilitate the management of
This Bash script is designed to facilitate the management of iptables firewall rules. It provides a more user-friendly command-line interface for listing, adding, and deleting iptables rules.
Windows Audit Cve Provider
 In the world of detection engineering, we often rely on heuristics to find anomalies. But what if the operating system could tell us directly: “Hey, someone
just tried to exploit this specific/critical vulnerability”?
In the world of detection engineering, we often rely on heuristics to find anomalies. But what if the operating system could tell us directly: “Hey, someone
just tried to exploit this specific/critical vulnerability”?