In this article we will dive into Cyber Kill Chain and MITRE ATT&CK. After getting comfortable with both frameworks, a short combination of both will be shown. The fishbone model is still under construction.
Cyber Kill Chain® Framework
As a first step, let’s talk about the Cyber Kill Chain® Framework. The framework itself was developed by Lockheed Martin. It includes the different stages of common cyber attack, starting from the reconnaissance stage till the end goal stage. Most of the successful attacks which were performed by various APT (Advanced Persistent Threat) groups, or the “attack groups”, often adopt the end-to-end process of the Cyber Kill Chain as part of their methodologies. So it’s a good idea to be familiar with it. Disrupting attackers at any point in the cycle may help reduce the impacts of the attacks.
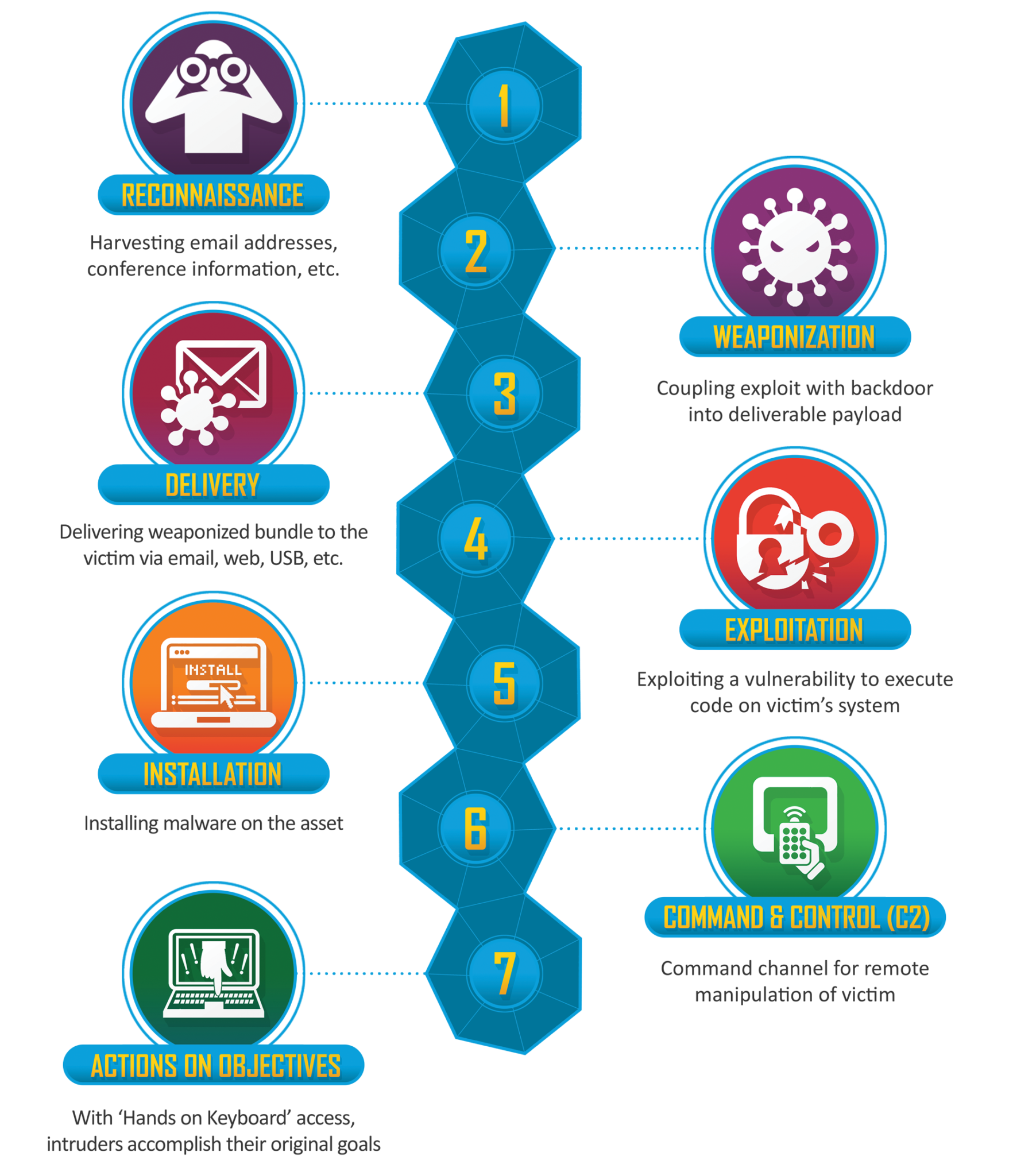
Let’s discuss the stages displayed in the process above:
- Reconnaissance — Adversary chooses the target, gathers information, and identifies vulnerabilities
- Weaponization — Adversary creates malware weapons to exploit vulnerabilities (e.g. virus, worm, etc.)
- Delivery — Adversary transmits weapon to selected target, using various methods (e.g. phishing, social engineering, compromised accounts, etc.)
- Exploitation — Adversary triggers malware to exploit target’s weakness
- Installation — Adversary performs installation (e.g. malware codes, modify security certificates, time bombs in system, etc.)
- Command & Control — Adversary remotely controls and manipulates target
- Actions On Objectives — Adversary performs actions to achieve their goals (e.g. data exfiltration/theft, data encryption for ransom, or data destruction)
MITRE ATT&CK® Framework
Now, let’s visit the MITRE ATT&CK® Framework in contrast. ATT&CK stands for Adversarial Tactics, Techniques, & Common Knowledge. This framework takes a deeper dive into the matrix that consists of various (cyber) attack techniques, categorized by tactics that adversaries/attackers can utilize to infiltrate your network and exfiltrate data. To walk through the framework take a look at my MITRE ATT&CK Bash Oneliner
To put it simply… · Tactics → WHY and WHAT an adversary is trying to accomplish · Techniques → HOW an adversary achieves a tactical objective
Below is a list of the tactics, with examples of the techniques and how organizations can mitigate them and disrupt attackers from achieving their goals:
-
Reconnaissance: Attacker gathers information to utilize and plan future operations
Gather Victim Identity Information — Organizations should place more efforts in limiting the amount of sensitive data available to external entities.
-
Resource Development: Attacker tries to establish resources to support operations
Pre-compromise — Unfortunately, this tactic cannot be easily mitigated as it includes actions performed by the attackers outside the scope of the organization’s defenses and controls.
-
Initial Access: Attacker tries to get into your network
Phishing — Organizations should have antivirus/antimalware software to detect and protect against malware. They can also provide user training for their employees to help them identify malicious emails from phishing campaigns and social engineering techniques.
-
Execution: Attacker tries to run a malicious code
User Execution — Organizations should have network intrusion prevention systems where they perform scans to remove malicious email attachments and links. Again, they should train their employees to identify and raise those potentially malicious events.
-
Persistence: Attacker tries to maintain their access into your system)
Account Manipulation — Orgs should have Multi-Factor Authentication (MFA) for their employee accounts to prevent attackers from preserving their access to compromised accounts.
-
Privilege Escalation: Attacker tries to gain higher-level permissions
Valid Accounts — Orgs should ensure that they have strong privileged account management, where they carefully assess the creation, modification, use, and especially the permissions of those accounts.
-
Defense Evasion: Attacker tries to avoid being detected
Impair Defenses — Orgs should restrict file and directory permissions, registry permissions, and have strong user account management to prevent attackers from disabling or interfering with security and logging services.
-
Credential Access: Attacker tries to steal account names and passwords
Brute Force — Orgs should follow the best practices for account use policies, password policies, and user account management to detect and prevent attackers from gaining access to credentials. Again, MFA is also an essential component.
-
Discovery: Attacker tries to figure out your environment
Account Discovery — Orgs should have strong operating system configurations to prevent unauthorized disclosure of account lists the attackers can use to support their attacks. This could be achieved by hardening based on CIS Benchmarks
-
Lateral Movement: Attacker tries to move through your environment
Exploitation of Remote Services — Orgs should follow the best practices for their network segmentation to reduce access to critical systems and services for the attackers to access remotely. Orgs should also perform frequent software updates and vulnerability scans to mitigate remote exploitations.
-
Collection: Attacker tries to inconspicuously gather data of interest based on their goals
Archive Collected Data — Orgs should have strong audit measures to identify potential weaknesses. In this scenario, to identify unauthorized archival activities.
-
Command and Control: Attacker tries to communicate with compromised systems to control them
Web Service — Orgs should restrict web-based content to prevent employees from accessing certain external services. This is crucial since attackers can essentially conceal their activities through popular social media and websites.
-
Exfiltration: Attacker tries to steal gathered data
Exfiltration Over Web Service — Again, orgs should restrict web-based content since popular web services can act as a cover and protection for the attackers while stealing the data
-
Impact: Attacker tries to manipulate, interrupt, destroy your systems and data
Data Destruction — Orgs should have data backup plans to recover and restore data, while ensuring that backups are unavailable and untouchable to the attackers.
If you are interested, take a look at the vast amounts of techniques the attackers can use for each tactic.
In a nutshell, the ATT&CK® Framework is backed up by many real-world observations and findings and is constantly updated to help organizations to “understand their adversaries”. Essentially, it provides insights on how attackers can potentially get in, avoid being caught, and manipulate, interrupt, or destroy critical organization assets/resources.
Cyber Kill Chain® meets MITRE ATT&CK®
The term Cyber Kill Chain is also used by various organizations besides the one from LockHeed Martin (Gartner, Varonis, SANS). Those models are all having slight variants but are based on the original one. That might confuse, even more if you assume there is only one Cyber Kill Chain model. With the knowledge based on MITRE ATT&CK this confusion might gets increased further and ask yourself, how they fit together.
One of the reasons why they can be so confusing to new learners with Penetration Testing background is because they are more or less derived from a typical Penetration Testing workflow. Anyone with Penetration Testing background could be bluffed by them with terms “model”, “kill chain”, “APT” and “weaponization”.
For the sake of simplicity, and completeness at the same time, the baseline of all known Kill Chain Models is added as a root node into the Fishbone Diagram below. All nodes are also enriched with MITRE ATT&CK Tactics and Techniques.
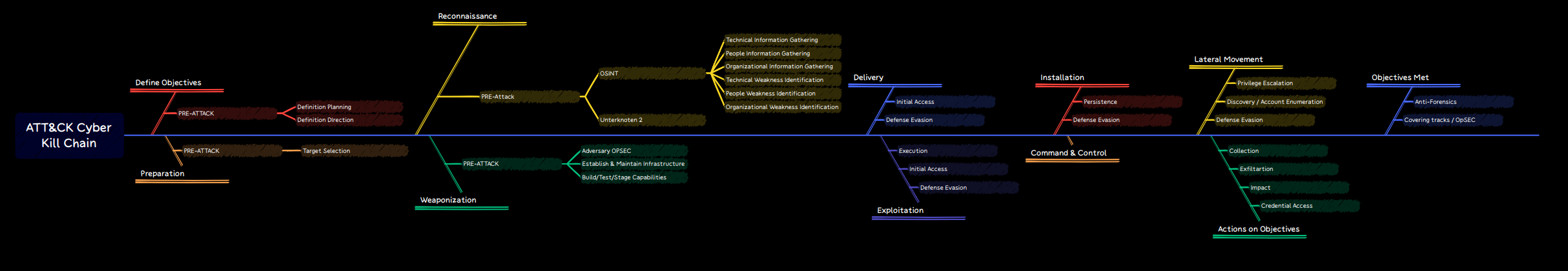
Get the more detailed Version: