This playbook will help you introduce effective DevSecOps practices in your company, regardless of size. We provide explicit guidance and actionable steps to introduce security controls, measure their effectiveness, and demonstrate value for money to your business leaders. Following this playbook will help teams build materially more secure applications, and that in the end, is the intent.
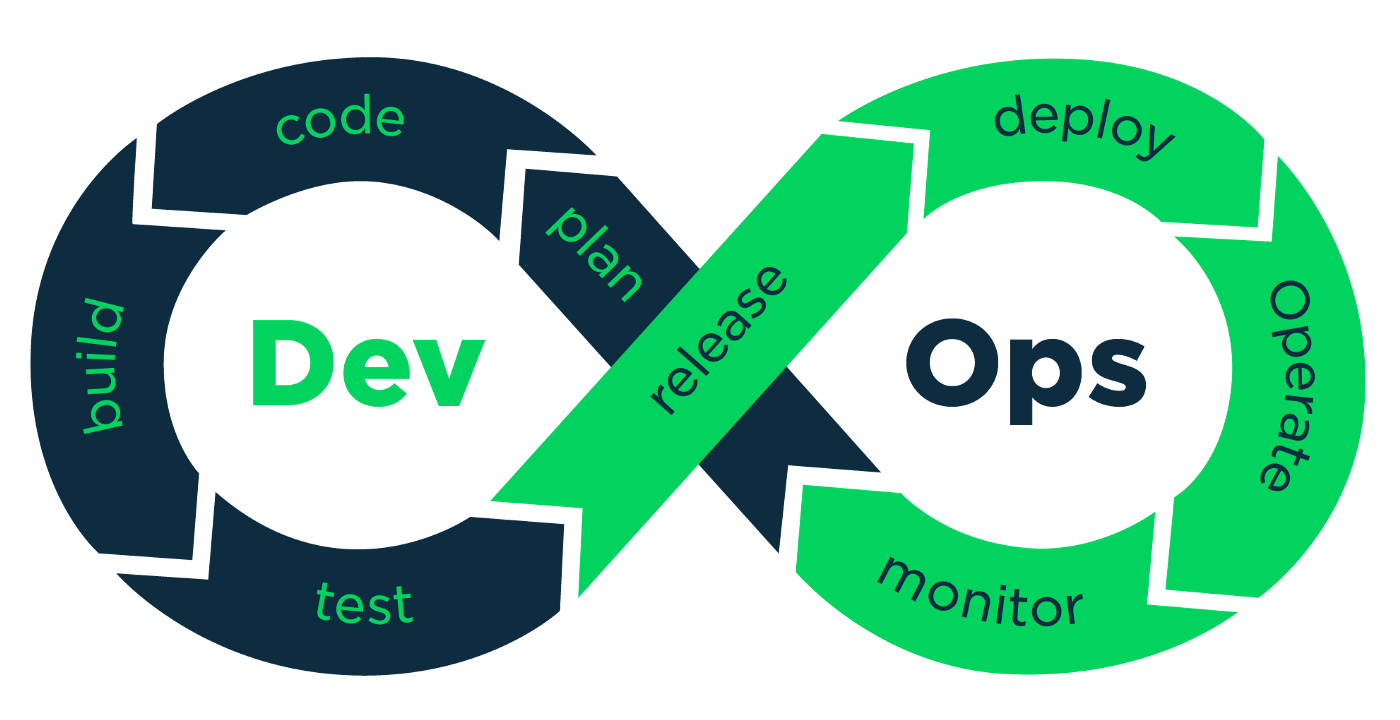
Agile is our Mindset - DevOps is our Culture
Dev(Sec)Ops Maturity Models
Maturity Models
Continuous Cloud Security
In this article you can follow me on my journey on how to master my way to something I call “Continuous Cloud Security”.
The CALMS Model of DevOps
CALMS is an acronym for Culture-Automation-Lean-Measurement-Sharing and a foundational model for DevOps.
The three ways of DevOps
If we think of DevOps there are plenty definitions, theories and more around. Also the 5 ideals of DevOps are an amazing piece of culture. But in my opinion, the best baseline to get in touch with DevOps are these books and the DORA State of DevOps reports from awesome authors like Gene Kim, Kevin Behr, Jez Humble and Nicole Forsgren:
Evil User Stories
 User Stories are an awesome part of XP (eXtreme Programming) and a really big achievement in leverage user centric thinking.
If you think of regular user story template you surely have found one like this:
User Stories are an awesome part of XP (eXtreme Programming) and a really big achievement in leverage user centric thinking.
If you think of regular user story template you surely have found one like this:
(S)SDLC
Goal of SDLC
Security can no longer be “outsourced” to the security team, but rather that the security team’s mission changes to providing the resources for teams to be security self-sufficient
Threat Modeling
 Threat Modeling works to identify, communicate, and understand threats and mitigations within the context of protecting something of value.
Threat Modeling works to identify, communicate, and understand threats and mitigations within the context of protecting something of value.
A song of entropy and toil
Prologue - or what is entropy?
Performing a Security Code Review
Code Reviews are required for auditing an application’s source code by people other then the author